Deploying a server | {Part-2}
In the previous series, we discussed about installing updates, setting timezone, changing hostname and more in detail. Today in this series we will be discussing about firewall setup.
Let’s first get to know about firewall. It’s a security system that monitors and controls incoming and outgoing network traffic based on predefined rules.
Firewall in real world scenario
Imagine you are a teacher in a classroom, and you want to make sure that only authorized people (students and staff) are allowed to enter the classroom, while keeping unauthorized people (such as strangers) out.
To achieve this, you could implement a firewall at the classroom entrance. The firewall would act as a gatekeeper, examining everyone who tries to enter the classroom and deciding whether to allow or block them based on a set of predefined rules.
For example, you might allow students and staff with a valid ID card to enter the classroom, but block anyone who doesn’t have an ID card or who presents a fake ID. You might also block anyone who tries to enter the classroom carrying prohibited items, such as weapons or drugs.
In this scenario, the firewall would act as a security system, protecting the classroom from unauthorized access and potential threats. By monitoring and controlling who is allowed to enter the classroom, the firewall can help ensure the safety and security of everyone inside.
Iptables
Ubuntu comes with builtin firewall called iptables. It is a command line tool in linux that helps you control the traffic that enters and leaves your computer.
iptablesis implemented as a kernel module in Linux, which means it runs directly in the operating system kernel.When network traffic arrives at the network interface of your computer, the kernel examines the traffic and compares it against the firewall rules stored in memory. If a packet matches one of the rules, the kernel takes the appropriate action based on the rule, such as allowing or blocking the traffic.ufw
It stands for Uncomplicated Firewall. The reason why we choose ufw is because of it’s user friendly interface for managing iptables in ubuntu and other debian based distributions. UFW is built on top of iptables which will allow you to create and manage firewall rules.
To use ufw you first have to enable it in your machine. You can do this by using the command
sudo ufw enable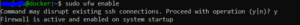
Setup default policies so that all incoming connection are denied.
sudo ufw default deny incoming
sudo ufw default allow outgoing.Denying incoming traffic will block all incoming traffic to your system will be blocked. Now any new SSH connection to your system is blocked. The current SSH connection won’t be loosed because it is considered outgoing traffic from your system.
How to allow SSH from my network?
Here’s how you can allow SSH connection from your network.
sudo ufw allow from [your_ip] to any port 22 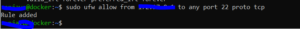
You can view the firewall rules using the command sudo ufw status . The result will look like this:
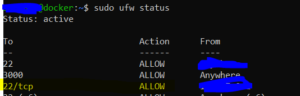
How to allow my https traffic?
Here’s how you can allow https from anywhere in your machine.
sudo ufw allow httpsSimilarly, you can view the rules using sudo ufw status
How to delete rules?
If you by mistake allowed any ports in your machine like i did, you can instantly delete the rules using the command.
sudo ufw delete allow [port]
#I have to do this
sudo ufw delete allow 3000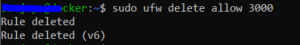
Aren’t there any other ways to delete rules?
Yes there is other way you can delete rules. First, you can list the firewall rules in numbered format using the command sudo ufw status numbered
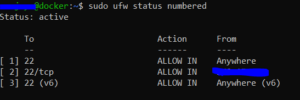
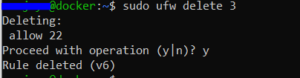
In the image above i have to delete the rule 3 because it’s allowing ipv6 SSH connection from anywhere that means anyone can do just ssh root@[IPv6_address] . To delete this rule i can do
sudo ufw delete 3 and the rule will be deleted.
And it’s the end of the part-2 series. In upcoming series, i will be taking you to fail2ban, live patching, and many other configurations. Thanks for staying.
If you want to read the previous part you can find the link below:
To further explore our expertise, check out our popular articles below:
- Basic linux commands: https://secnep.com/basic-linux-commands/
- Redhat image builder: https://secnep.com/pushingimagetogcp/
References Link:
- Ubuntu Documentation – https://ubuntu.com/server/docs/security-firewall
- Livepatch Ubuntu – https://ubuntu.com/livepatch
- DigitalOcean’s Firewall Guide – https://www.digitalocean.com/community/tutorials/how-to-set-up-a-firewall-with-ufw-on-ubuntu-18-04
- How To Configure A Firewall Using Iptables – https://www.digitalocean.com/community/tutorials/how-to-configure-a-firewall-using-iptables-on-ubuntu-18-04
Fantastic beat I would like to apprentice while you amend your web site how could i subscribe for a blog site The account helped me a acceptable deal I had been a little bit acquainted of this your broadcast offered bright clear concept
Thank you for the good writeup It in fact was a amusement account it Look advanced to far added agreeable from you However how could we communicate
Wonderful web site Lots of useful info here Im sending it to a few friends ans additionally sharing in delicious And obviously thanks to your effort